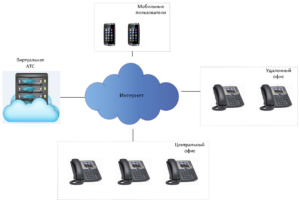
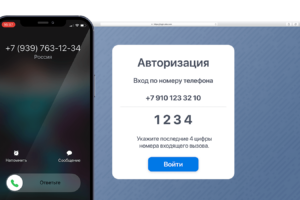
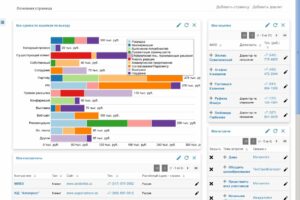
На примере сервиса Ucaller, предоставляющего такой сервис, можно увидеть, что доставлять коды можно двумя
Основы ценообразования в платном хостинге скрыты за множеством факторов. В первую очередь, стоимость зависит
Regfon, как комплексное решение, включает услуги по продаже/аренде виртуальных номеров, ВАТС и оборудования для
Ниже — обзор популярных сервисов авторизации по звонку, с помощью которых вы сможете быстро
uCaller — программное обеспечение, позволяющее упростить авторизацию покупателей в онлайн-магазинах, сделав ее приятнее для
С его помощью вы сможете объединить в одно окно мессенджеры WhatsApp, Facebook, Instagram, Telegram,
SuiteCRM — это самая популярная в мире CRM-система с открытым кодом, подходящая для решения
Продукт выпущен отечественной компанией с 20 летним стажем разработки программ и состоящей в «Едином
Омниканальная связь обеспечивает лучший клиентский опыт, позволяя потенциальным и действующим заказчикам переключаться между каналами связи,
Отличительной особенностью провайдера является стратегия взаимодействия с клиентами, которая строится на потребностях каждого отдельного
Если вам нужно разместить физический сервер в надежном дата-центре или арендовать виртуальный облачный сервер,
Интеграции позволяют быстро и просто объединять различные компоненты IT-инфраструктуры в единую систему, например, CRM
ActiveCloud – компания с офисами в России и Беларуси, работающая в сфере хостинг услуг
ANYSERVER — компания, занимающаяся поставками серверного б/у оборудования из Европы. За 10 лет работы она
Для компаний, оказывающих услуги проката велосипедов, есть отличный вариант авторизации клиентов звонком по коду
Авторизация по коду в голосе для фитнес-центров и салонов красоты поможет сделать взаимодействие клиентов
Если вам нужен действительно надежный хостинг или VPS-сервер, обратите внимание на провайдера CloudVPS.
Общение с клиентами — это одна из основополагающих вещей, влияющих как на успех компании,
С февраля 2022 года многие производители серверного оборудования прекратили поставки в Россию. Среди них
Согласно исследованию Data Insight, опубликованному в марте 2023 года, объем российского рынка интернет-торговли за
Большое число каналов связи позволяет увеличить количество обращений клиентов, повысить их вовлеченность в общение
При внедрении CRM-системы бизнес может рассчитывать на существенное улучшение качества процессов в компании, эффективности
MPSpace – сервис с биддером для Вайлдбериз, который работает с 2021 года, но уже
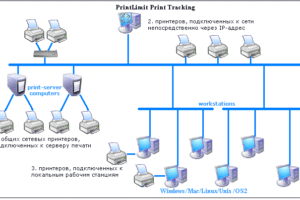
Хостинг-провайдер HostiMan предлагает хостинг, аренду серверов и множество других услуг. Компания работает в данной сфере
При выборе хостинга для сайта автосервиса (после консультаций со спецами, конечно же) решил, что
Компания vpn.how предлагает VPN серверы с неограниченным трафиком в разных странах мира. Заказанный сервер создается в
Здесь предлагают услуги с учетом всех актуальных тенденций в данной сфере и потребностей веб-проектов
FourServer – относительно молодой (начал работать в 2017 году), но достигший впечатляющих результатов сервис, предлагающий
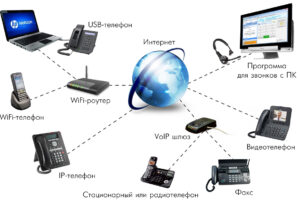
Авторизация по коду в голосе – относительно новая технология, которая подразумевает озвучивание кода голосом.
Сервис «Тебе зачёт» - это гарантия выполнения задачи и высокое качество, подтвержденное оценками клиентов.